My CRTS Feedback

What's CRTS ?
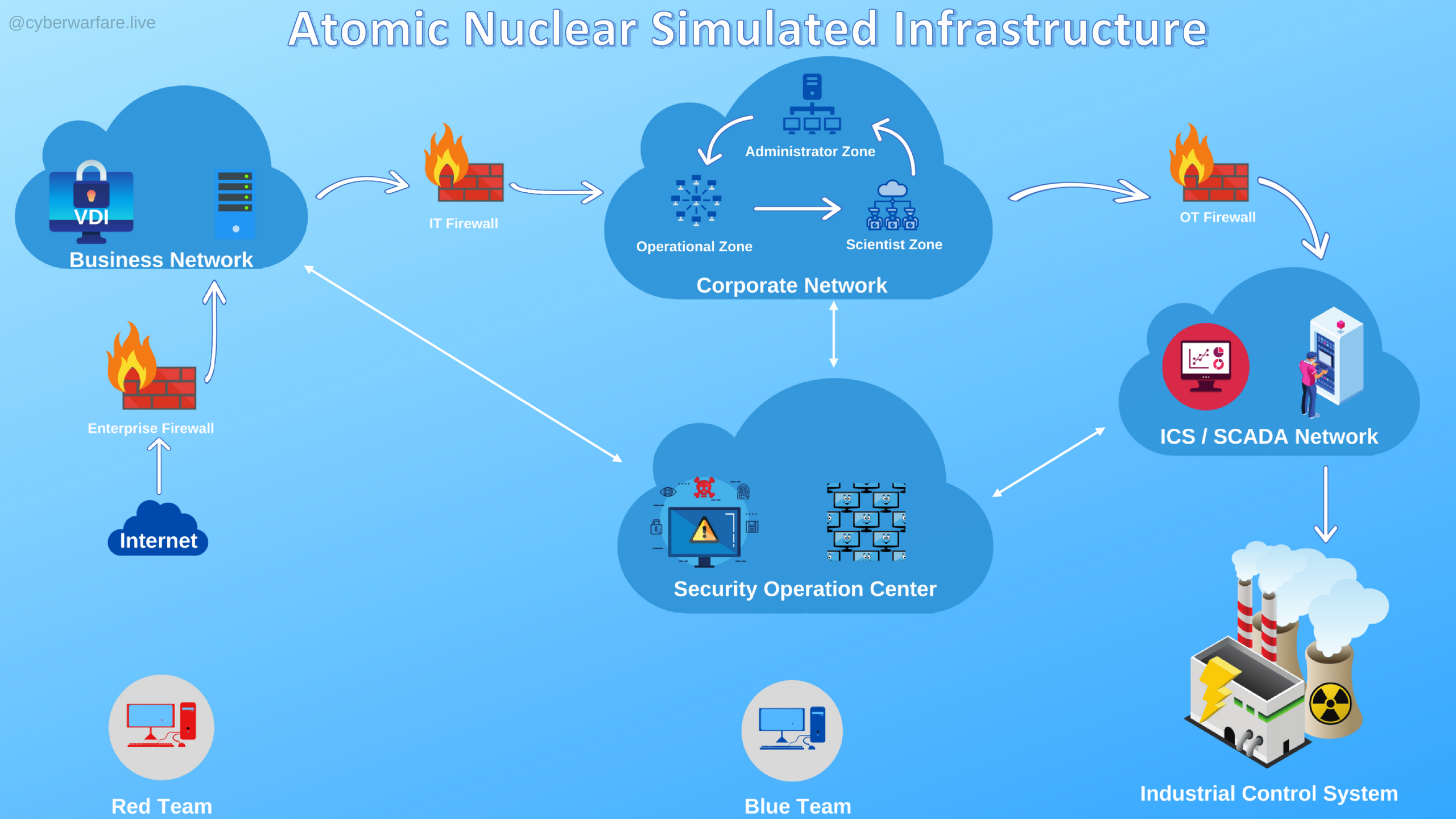
My Experience
Well, this certification turned out to be quite a surprise for me. Initially, I wasn't expecting much beyond a simple lab, and then it transformed into an incredibly engaging experience. The internal lab setup was so well-done that I found it truly enjoyable!
You have the freedom to choose any attack path you prefer. I went with the first one, which involves a Web attack. Once you compromise the web server, you're required to pivot into another internal Active Directory network. Once you compromise the domain, you're faced with yet another pivot to an internal Active Directory network linked through a Trust Forest design. Let me tell you, after completing this lab, I became a pro at pivoting and post-exploitation on Active Directory!
The cherry on top is gaining access to a complete SCADA network – personally, that was the most satisfying reward for me!
And don't forget about the attack on Kubernetes and Docker containers; it's a fascinating aspect since you don't often get to play around with them in real pentesting engagements!
Worth It ?
In my case, I followed my instincts for the initial attack path. When I hit roadblocks, I turned to the writeup, especially for machines that I wasn't particularly comfortable with, like the Kubernetes (K8S) and the intensive pivoting parts.