#Binary 1.2 - Linux ret2win 32-bit

ROP 32 ?
A ROP 32 works in the same way as a buffer overflow except that there is no shellcode here!
The purpose of a ROP 32 is to call a function of the program that is never called once in the program code.
In this tutorial I will show you how to execute a ROP exploit on a 32bits binary.
Code
Here is the code of the program we are going to use:
If you followed the tutorial on bufferoverflow, the code is almost the same.
The only difference is the addition of an extra function win() but as you can see, this function is never called in the program.
Compile
To compile it, we use gcc with the following options:
Disable ASRL :
Padding
First, we need to find the padding to fill the EIP register.
For this we use a pattern with gef.
Once the pattern is created we will use it in our program to make it crash:
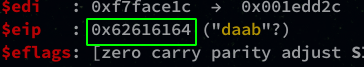
We get the offset present in EIP and we use the following command to find the size of EIP:
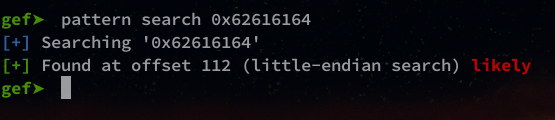
The adding will be 112.
The win function
Now we’ll get the address of the win() function.
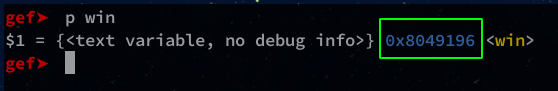
We are ready to pwn !
Exploit !
We will use a python script to generate our payload:
Exec and win !
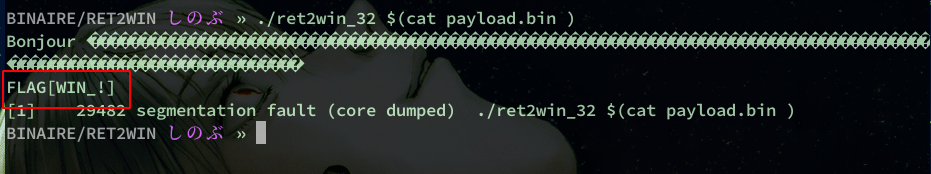
Now our function has been called!