#8 Nsec21 - Tom's Hut part1

The next 2 Flags are binary reverse, I was very very rusty on this one …
Wi-Fi Join
So, this challenge is accessible from Tom’s Hut after you have joined a Wi-Fi network !
To join a Wi-Fi network, you need to access the serial port using screen (check Chall 7 !) and use the following command:

You should receive an IP, you can now go to Tom’s Hut and see the following message !
Download both of the binaries, RE101 and RE102.
RE101 - Reverse
The first binary named re101.elf is a binary using Xtensa architecture.

Xtensa Processor
I can´t execute it on my machine so I’ll use Ghidra to dissas and take a look inside.
Unfortunately Ghidra can’t understand Xtensa binaries by default, so I need to add an extra Processor, here is the github link
The install is explained inside the README.md but becarefull to gve your user the full ownership of the xtensa folder.
Now the binary is recognized, we can analyse it and reverse it !
Main function
The main function is easly located in the ghidra function folder.

As we can see, this function accept a user input and then check this input with verify function. Depending of the user input, the verifyfunction will display the flag or not.
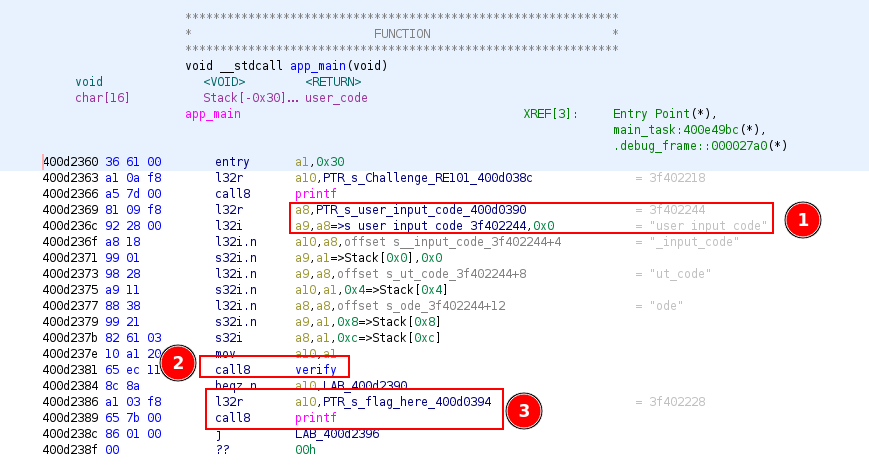
Verify !
The main function won´t give us more information so let’s dig into verifyfunction !
This one is a bit tricky but after half an hour, I sort of understand how it works.
So, the user input in a1 is checked characters by charaters but not in the right order.
The characters that are compared are stored inside a3, a8 etc. and the value of these registers are changing during the execution of the binary.
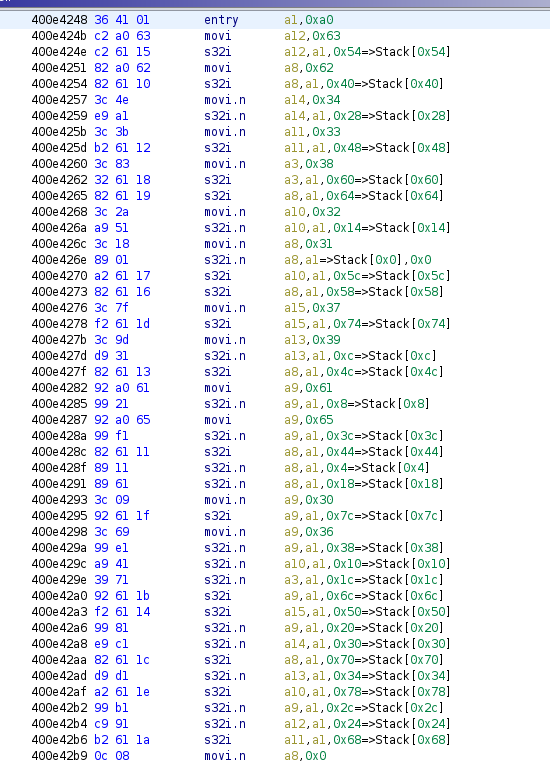
I was a bit lazy on this one and used a notepad to check characters by characters the user input and then found the FLAG.
Here is the correct order for each check.
So you have the value a something with the affected value using movi. Then the Stack whith the position of the letter checked inside the user input and it’s value.
400e4248 36 41 01 entry a1 = 'u'
400e424b c2 a0 63 movi a12 = 'c'
400e424e c2 61 15 s32i a12,a1,0x54=>Stack[0x54] ---> 22 = c
400e4251 82 a0 62 movi a8 = 'b'
400e4254 82 61 10 s32i a8,a1,0x40=>Stack[0x40] ---> 17 = b
400e4257 3c 4e movi.n a14 = '4'
400e4259 e9 a1 s32i.n a14,a1,0x28=>Stack[0x28] ---> 11 = 4
400e425b 3c 3b movi.n a11 = '3'
400e425d b2 61 12 s32i a11,a1,0x48=>Stack[0x48] ---> 19 = 3
400e4260 3c 83 movi.n a3 = '8'
400e4262 32 61 18 s32i a3,a1,0x60=>Stack[0x60] ---> 25 = 8
400e4265 82 61 19 s32i a8,a1,0x64=>Stack[0x64] ---> 26 = b
400e4268 3c 2a movi.n a10 = '2'
400e426a a9 51 s32i.n a10,a1,0x14=>Stack[0x14] ---> 6 = 2
400e426c 3c 18 movi.n a8 = '1'
400e426e 89 01 s32i.n a8,a1=>Stack[0x0],0x0 ----> 1 = 1
400e4270 a2 61 17 s32i a10,a1,0x5c=>Stack[0x5c] ---> 24 = 2
400e4273 82 61 16 s32i a8,a1,0x58=>Stack[0x58] ---> 23 = 1
400e4276 3c 7f movi.n a15 = '7'
400e4278 f2 61 1d s32i a15,a1,0x74=>Stack[0x74] ---> 30 = 7
400e427b 3c 9d movi.n a13 = '9'
400e427d d9 31 s32i.n a13,a1,0xc=>Stack[0xc] ----> 4 = 9
400e427f 82 61 13 s32i a8,a1,0x4c=>Stack[0x4c] ----> 20 = 1
400e4282 92 a0 61 movi a9 = 'a'
400e4285 99 21 s32i.n a9,a1,0x8=>Stack[0x8] ------> 3 = a
400e4287 92 a0 65 movi a9 = 'e'
400e428a 99 f1 s32i.n a9,a1,0x3c=>Stack[0x3c] ---> 16 = e
400e428c 82 61 11 s32i a8,a1,0x44=>Stack[0x44] ---> 18 = 1
400e428f 89 11 s32i.n a8,a1,0x4=>Stack[0x4] -----> 2 = 1
400e4291 89 61 s32i.n a8,a1,0x18=>Stack[0x18] ---> 7 = 1
400e4293 3c 09 movi.n a9 = '0'
400e4295 92 61 1f s32i a9,a1,0x7c=>Stack[0x7c] ---> 32 = 0
400e4298 3c 69 movi.n a9 = '6'
400e429a 99 e1 s32i.n a9,a1,0x38=>Stack[0x38] ---> 15 = 6
400e429c a9 41 s32i.n a10,a1,0x10=>Stack[0x10] ---> 5 = 2
400e429e 39 71 s32i.n a3,a1,0x1c=>Stack[0x1c] ---> 8 = 8
400e42a0 92 61 1b s32i a9,a1,0x6c=>Stack[0x6c] ---> 28 = 6
400e42a3 f2 61 14 s32i a15,a1,0x50=>Stack[0x50] ---> 21 = 7
400e42a6 99 81 s32i.n a9,a1,0x20=>Stack[0x20] ---> 9 = 6
400e42a8 e9 c1 s32i.n a14,a1,0x30=>Stack[0x30] ---> 13 = 4
400e42aa 82 61 1c s32i a8,a1,0x70=>Stack[0x70] ---> 29 = 1
400e42ad d9 d1 s32i.n a13,a1,0x34=>Stack[0x34] ---> 14 = 9
400e42af a2 61 1e s32i a10,a1,0x78=>Stack[0x78] ---> 31 = 2
400e42b2 99 b1 s32i.n a9,a1,0x2c=>Stack[0x2c] ---> 12 = 6
400e42b4 c9 91 s32i.n a12,a1,0x24=>Stack[0x24] ---> 10 = c
400e42b6 b2 61 1a s32i a11,a1,0x68=>Stack[0x68] ---> 27 = 3
400e42b9 0c 08 movi.n a8 = '0'
Flag
So, at the end, with all the position in the right order, here is the flag
- Flag =
11a922186c46496eb1317c128b361720
We can validate the challenge using the CLI on the badge
